
techietraveller84
-
Posts
209 -
Joined
-
Last visited
Content Type
Profiles
Forums
Downloads
Posts posted by techietraveller84
-
-
One of the reasons I want to move to SE Asia is so I can have geckos living in my home.
They provide free pest control and occasional funny stories.
How loud are they though?
-
 1
1
-
 1
1
-
-
Here's how some people are getting it; not recommended.
QuoteA new type of fraud is spiking across the (Telegram) platform: Selling fake vax records to people who want to lie their way into places where proof of vaccine is required.
Telegram groups are being abused by fraudsters peddling fake COVID-19 vaccination cards to the unvaccinated and anti-vaxxer communities, according to researchers.
Brittany Allen, trust and safety architect at Sift, noticed the illicit sales on the encrypted messaging platform as the COVID-19 vaccination began to ramp up earlier in the year. Several groups circulating on Telegram specialize in different types of fraud, including selling stolen credentials or credit-card numbers, as well as guides to how to defraud certain companies. Lately though, fraudulent vaccination cards have become a hot commodity, she said.
https://threatpost.com/telegram-forged-covid-19-vaccine-cards/166093/?web_view=true
-
How's the old gentleman able to spend each day every day at the airport and not attract the attention of law enforcement? Wonder if he's a Thai Visa member as well...
-
- Popular Post
- Popular Post
People still not following mother's advice: "if it's too good to be true..."
QuoteA cryptocurrency scam recently pilfered at least $2 million from WallStreetBets enthusiasts, convincing them that they were buying into a new crypto coin connected to the popular memestock, according to a report from Bloomberg News.
For weeks, moderators of the notorious Reddit forum have warned users to avoid fraudulent scams based around the good WSB name. A post, tethered to the top of the group’s page, asks community members to be wary of offers related to WSB products.
Apparently, a lot of people missed this memo, because a bunch of WSB fans reportedly fell for a scam of exactly this ilk. Indeed, an offer recently began circulating on chat app Telegram, peddled by an account called “WallStreetBets - Crypto Pumps.” This “Crypto Pumps” said it was offering a chance for bets enthusiasts to cash in on a new WSB crypto-token, dubbed “WSB Finance,” before it officially launched. In the crypto world, an arrangement like this is called a “premine sale”—an opportunity for early investors to buy up a token before it hits the crypto exchanges and gets a more widespread, public release.
Interested parties were instructed to send Binance Coin or Ether to a crypto wallet, then get in touch with the page’s “token bot,” which would send the user WSB Finance tokens. What a good deal! It wasn’t long before the ETH and BNB were pouring in, swelling Crypto Pump’s wallet.
However, buyers ran into a little snag. Not long after the coinage was pocketed, “Pumps” told them that there had been a problem with the bot—it was malfunctioning. As a result, users should send more crypto payments, or they would “lose their initial investment,” Bloomberg reports.
https://gizmodo.com/scammers-score-2-million-from-the-wallstreetbets-crowd-1846829132?&web_view=true
-
 3
3
-
14 hours ago, fdsa said:
well, you are uncovering the much deeper issue: the apps, companies and governments are being built insecure from the very beginning and do not even want to become secure.
and the reason is: a human factor (ignorance multiplied by lack of competence plus overall lazyness).
Maybe China's got it figured out then: remove the human factor.
Today's headline in Nikkei Asia: Robots will make doubling China's GDP by 2035 look easy
-
To escape your world, I think a lot of people would elect the below punishment. Hawaii please?
QuotePeople with extreme and radical views would be banished to special rehabilitation camps housed on isolated remote islands.
-
Your passwords can be brilliant concoctions of dozens of symbols that are unbreakable. Won't do much for you though at the rate with which apps, companies and governments are getting virtually violated.
I'm still going to keep my passwords crazy, but I fully expect to get completely exposed online sooner or later. Two confidence reducing headlines from the last couple days:
Unsecure Apps: Over 40 Apps With More Than 100 Million Installs Found Leaking AWS Keys
Government cyber defense fails: 345,000 files from Filipino solicitor-general's office were breached
-
 1
1
-
-
Reduce the paper trail as much as possible, and like Jingthing mentioned, do that by having the money deposited in a different country, and avoid anything that's clearly illegal.
I'd imagine the market for online teaching in China is pretty hot right now since the borders are essentially closed, cutting off their supply of fresh EFL meat.
-
 2
2
-
-
Different story, but in similar feel-good topic, another bad guy in the hacker world has been arrested and sentenced.
Still though, why do I have the feeling he'll still be running crime from prison?
QuoteA high-level manager of cybercrime group FIN7, also known as the Carbanak Group and the Navigator Group, has been sentenced to ten years in prison, the Department of Justice reports.
FIN7 has operated since at least 2015 and had more than 70 people organized into business units and teams.. While its activity is global, in the United States, FIN7 has breached corporate computer networks in all 50 states and the District of Columbia. Attackers have stolen more than 20 million payment card records from at least 6,500 point-of-sale terminals at more than 3,600 businesses.
Ukrainian national Fedir Hladyr was a systems administrator for FIN7. He was arrested in Dresden, Germany in 2018 at the request of US law enforcement. In 2019 he pleaded guilty to conspiracy to commit wire fraud and one count of conspiracy to commit computer hacking.
To conduct its attacks, FIN7 wrote emails to appear legitimate to an organization's employees and followed up with phone calls to further legitimize their activity. When an email attachment was opened, FIN used a modified version of the Carbanak malware, in addition to other tools, to steal customers' payment card data. Much of this data has been sold on the Dark Web.
As systems administrator for FIN7, Hladyr played a core role in aggregating stolen data, supervising other criminals in the group, and maintaining the network of servers that FIN7 used to target and control victims' machines. He also handled FIN7's encrypted communication channels, officials report.
-
Now I see why he was called "the snake."
https://www.oxygen.com/true-crime-buzz/where-is-suspected-serial-killer-charles-sobhraj-now
QuoteInvestigators have estimated that Sobhraj killed between 12 and 20 people, The Los Angeles Times reports. In his interviews with Neville and Clark, he initially admitted to at least 12 killings between 1972 and 1976, though he later recanted, CNN reports. He claimed to have committed his first murder in 1972 by killing a taxi driver while in Pakistan. While he was never charged with the murder, he was behind bars in various countries at least five times for lower level offenses before he was officially suspected of murder. He also escaped jail at least four times, according to CNN. He escaped an Afghanistan jail for robbery by faking illness and drugging guards in 1972. He escaped an India prison a year later by again faking illness. Then, in 1975, he escaped incarceration by setting fire to a prison van.
His first murder charge came in 1976 when Sobhraj was caught in New Delhi drugging students, according to the Los Angeles Times. He was charged with both robbery and the murders of an Israeli man, Alan Aaron Jacobs, in Varanasi and a French tourist in New Delhi. He was found guilty of both robbery and murder, but the murder convictions were later overturned on appeal. He was incarcerated from 1976 to 1997, during which time he was apparently treated like royalty. He was given multiple cells and privileges, according to journalist Alan Dawson, who interviewed Sobhraj in 1984. He also managed to briefly escape prison again in 1986 by drugging guards with laced fruit, claiming it was his birthday.
-
What happened to the title of this thread? Is it just me, or is something a bit off?
Quotebecause of virus outbreak CORONAVIRUSPublished 18 hours ago How will we know we've reached herd immunity?
-
15 minutes ago, faraday said:
Anybody in custody...?
Good question. Looks like it was a Russian site, most likely used by the Russian speaking hacking community. Not sure how they handle things like this over there.
-
 1
1
-
-
More good news, kind of. Another hacker forum was well, hacked, exposing "12,344 sets of data for card shop admins, sellers and buyers, including user names, hashed passwords, contact details, sales activity and current balances."
At the same time though, the "database also has 498 sets of (stolen) online banking account credentials and 69,592 sets of U.S. Social Security Numbers and Canadian Social Insurance Numbers."
https://threatpost.com/623m-payment-cards-stolen-from-cybercrime-forum/165336/
-
I don't know the answer, but actually have the same question. Were you able to find out?
-
What usually happens to foreigners caught doing this kind of business? Worse or more lenient than punishment for Thais?
-
There is hope for a bit less cheating in the world of gaming.
QuoteChinese police have uncovered the world's biggest online video game cheat sales syndicate, netting luxury cars and millions of dollars in cryptocurrency during a string of arrests.
- Chinese police have arrested 10 people accused of selling the cheat software
- One was nabbed with more than $5 million in cryptocurrency and luxury cars
- Data shows there were 2.5 billion gamers playing in 2019 and they spent a total of $199.2 billion that year alone
-
23 hours ago, OneMoreFarang said:
In principle that is correct. But if people want that an app works what do they do? Click yes.
Unfortunately it is almost impossible to use any internet connected device today and don't give away lots of information. Do I like it? No. Could I do something against it? In part, with lots of effort. At least my summary is: forget it, accept it, that is "modern" life.
True. That's the price of being the product, I guess.
-
 1
1
-
 1
1
-
-
This study from Cybernews found that "the percentage of apps that needlessly ask for unrestricted access to our whereabouts, device usage, and communications is highly alarming, if not objectionable." Whether online privacy is a priority for you or not, I recommend learning about what permissions your apps have, because they might know a lot more about you (and be selling it to the highest bidder) than you care to share.
QuoteIn theory, Android app permissions are a great way to ensure our safety and protect our privacy. In practice, however, these permissions aren’t always shown prominently or described in much detail, and we may be completely unaware of the fact that we just gave a beauty camera app our full blessings to record audio, track our location, or go through our contacts list. In fact, some apps harvest our data even when we deny them access to personal information. And the situation seems to only be getting worse with each passing year.
With that in mind, we at CyberNews wanted to see if requests for dangerous permissions in Android apps are really getting out of control. To do this, we examined the top 1020 apps on the Google Play store and analyzed the permissions they were asking for.
What we found was rather alarming: requests for dangerous permissions were incredibly common among the top Android apps. Not only that, permissions that are particularly invasive, such as access to your camera, location, and microphone were frequently requested by apps in categories that should have no business asking for them.
In principle, app permissions are supposed to prevent others from violating your privacy by letting you control what data you give up. Sadly, when every other app wants to track your location or read you call logs, it seems that the principle might no longer hold true.
https://cybernews.com/privacy/android-apps-are-asking-for-too-many-dangerous-permissions-heres-how-we-know/ (or google the title, "Android apps are asking for too many dangerous permissions. Here’s how we know.")
-
 1
1
-
-
Since we are talking about Acer, today's side story is the company just got hit by a $50 million ransomware attack. Maybe justice for them making it so hard for you to take care of your friend's daughter's laptop. ????
QuoteComputer giant Acer has been hit by a REvil ransomware attack where the threat actors are demanding the largest known ransom to date, $50,000,000.
Acer is a Taiwanese electronics and computer maker well-known for laptops, desktops, and monitors. Acer employs approximately 7,000 employees and earned $7.8 billion in 2019.
-
 1
1
-
-
There's not a lot of good news in the cyber world these days, but today saw a story that brought a smile to my face.
QuoteA user on a popular hacker forum is selling a database containing highly sensitive information of more than 24,000 customers of the now-defunct illegal online service WeLeakInfo.

Before it was shut down by the FBI in January 2020, WeLeakInfo was a website that had been selling access to stolen information scraped from more than 10,000 data breaches, which contained over 12 billion indexed user credentials, including names, usernames, email addresses and passwords for online accounts.
The forum user is selling the highly sensitive information of former WeLeakInfo customers – including their full names, IP addresses, street addresses, and phone numbers – for about $2 in virtual forum currency.
What was leaked?
The author of the forum post is selling a ZIP archive that contains payment data of WeLeakInfo customers who made their illicit purchases via Stripe, including:
- Full names
- Partial credit card data
- Transaction dates and their Stripe reference numbers
- Currencies and amounts paid for stolen data
- Email addresses
- IP addresses
- User Agents (used to identify the browser/device used by the customer)
- Street addresses
- Phone numbers
How the data was acquired: an oversight by the FBI?
The user who is selling the WeLeakData archive on the hacker forum claims that the FBI might have missed a spot during the seizure of the original WeLeakInfo domain. According to the forum post author, there was a separate domain associated with the WeLeakInfo service that was used to process payments made by people who bought stolen data via Stripe. And it seems that the payment website was, inadvertently or not, allowed to expire in March 2021.
This means that after the website expired, anyone could have claimed the domain as their own. Which the cheeky forum user seemingly did on March 11.
The author claims they were then able to perform a password reset against the Stripe.com account that was potentially associated with one of the two owners of WeLeakInfo, and gain access to all the data from the website, which seems to have operated for less than a year and accumulated sales of a little over £100,000 from 24,603 customers.
Judging from the samples of data provided by the author, the age of the Stripe account owner is consistent with the FBI’s information about the arrested owners of WeLeakInfo.
-
 2
2
-
I was sure this thread would end with a link to a gold buying site or something similar. Happily proven wrong.
-
- Popular Post
Funny that they likely left the Royal Family spotlight to live more simple, quiet and anonymous lives, yet here they are on Oprah. I hear they've got a podcast as well. And a bunch of projects with Netflix. So much for a quiet life of anonymity.
I imagine the spotlight is addictive, and it's a hard thing to leave behind.
QuoteSpotify announced Dec. 15 that it had struck a multi-project deal with Archewell Audio, the couple's newly created podcast shingle. Their first full podcast series is expected to be released on Spotify in 2021.
The deal follows a similar pact between Harry and Meghan and Netflix, where they will produce documentaries, feature films and children's programming.
https://www.hollywoodreporter.com/news/prince-harry-meghan-markle-release-podcast-special-on-spotify
-
 6
6
-
12 minutes ago, rasmus5150 said:
Just a shame that most of these Heritage Sites charge foreigners (non Asian) 10X the entrance price.
Cannot start to imagine what would happen if any European country started charging guests by the color of their skin.
What color skin do foreigners have?
-
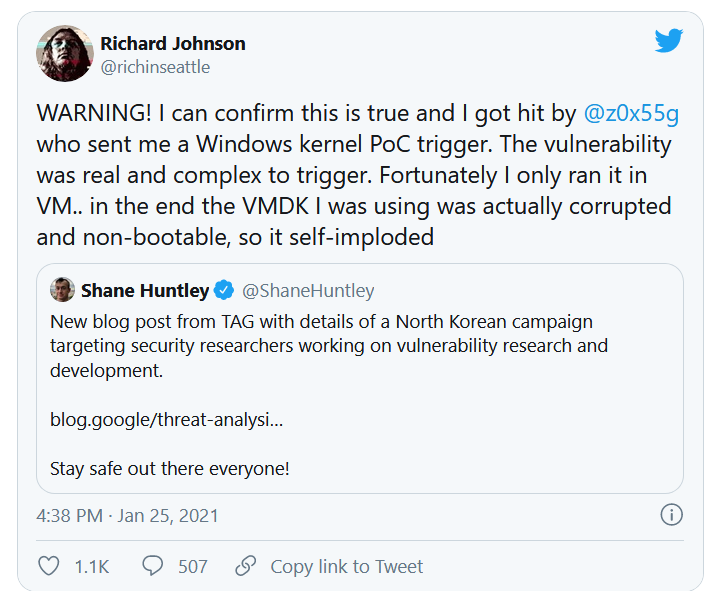
Source: https://safernet.it/state-sponsored-hackers-cybersecurity/
In January, it came to light that state sponsored hackers attacked US-Based cybersecurity researchers.
The attack was carried out via social engineering, followed by an attempt to install malware on the target’s machine, which would act as a backdoor. With this backdoor in place, the culprits would be able to gather intel on the researchers work; possibly around vulnerability the research community as a whole were working on.
Attack Methodology
In order to gain trust within the research community, the hackers created Twitter accounts – These were linked to their own “research” blogs. From these accounts they would share what you’d expect from a researcher – tweets on their own research including videos, retweets from other researchers, and links to their own blogs and others. These actions helped build credibility and a sense of legitimacy in their Twitter accounts.

As their blogs increased in popularity, they often had guest bloggers – Legitimate individuals from within the research community. This, again, helped the hackers credibility.
Once they had established themselves on Twitter, the next phase began. The hackers started to reach out to researchers on Twitter via private message.

The state sponsored hackers proposed to the target that they should collaborate on research together. Once the target seemed interested, the conversation would then continue via Telegram.
The collaboration was around vulnerability research, and the hacker would provide the target with a Visual Studio Project. Within the Project was the exploit source code, and a DLL. Upon installation, the DLL would immediately begin to communicate with domains controlled by the hackers. Together, these would provide a backdoor into the researchers machine.
It is currently unknown how many targets the attacks were successful on. One such target, cybersecurity researcher Richard Johnson, had run the Project on a Virtual Machine (VM), and was unscathed.

Additional Attack Vectors
Since details of the initial attacks became public, Google’s Threat Analysis Group (TAG) have identified a separate attack vector linked with the same state sponsored hackers.
The blogs created by the hackers were shared on numerous socials – Reddit, LinkedIn, Discord, and the aforementioned Twitter.
Specifically, one blog titled ‘DOS2RCE: A New Technique to Exploit V8 NULL Pointer Dereference Bug’ was shared from October 14th 2020 onward. It was discovered by Microsoft that the simple act of clicking the link to this blog would deploy malware to the victims browser. The malware would reach back to the hackers controlled domains and execute malicious javascript. It is thought that the attack was successful on a up-to-date versions of Chrome, leading Google to remark that it took advantage of a zero-day vulnerability.
It is suspected the attackers behind these events are a part of ZINC, which works under Lazarus Group. Lazarus Group first came into the public spotlight when they carried out Operation Troy, which ran between 2009 and 2012.
Operation Troy was a series of distributed denial-of-service (DDos) attacks targeting government establishments in Seoul, South Korea.
Lazarus Group made the news again, identifying themselves as ‘Guardians of Peace’, in November 2014 for carrying out the Sony Pictures hack. During the attack, confidential data of many Sony Pictures employees were released, and initially circulated on Reddit. This attack is notable in the history of Lazarus Group; it was carried out in a sophisticated and complex manner, showing the group were now developing their skills rapidly.
Lazarus Group have also been responsible for a number of digital bank-heists; and the amount seized is believed to be at least $97 million.
The WannaCry ransomware attack of 2017, which saw a number of healthcare systems including the NHS in the UK brought to a halt, is believed but not confirmed to have been carried out by Lazarus Group.
As of today, Lazarus Group are involved in a number of additional attacks, notable the late-2020 pharmaceutical company attacks. By using spear-phishing methods, members of Lazarus Group acted as health officials and reached out to a number of pharmaceutical companies. Once trust was gained, Lazarus Group sent a number of malicious links to the companies. It is unconfirmed what the goal of the attack was, but it is suspected that they were looking to sell data for profit, extort the companies and their employees, and give foreign entities access to proprietary COVID-19 Research.




Just in case you think Lazada reviews are genuine.
in General Topics
Posted
I know someone up the chain mentioned Amazon's problem with fake reviews, but this article goes into some detail on how the system works and where it may be based. It's likely the same people/companies/systems that operate the Lazada fake review services. The fake reviews ecosystem seems to be a large industry in China.
https://www.infosecurity-magazine.com/news/database-exposes-200k-fake-amazon/